Report: Threat hunting is more SOC than intel- Valutrics
Threat hunting is found mainly at larger enterprises in a handful of industries. A 2017 threat hunting survey of 306 IT and security professionals by the SANS Institute indicated that, at many organizations, the process is new and poorly defined. Hunting programs are more likely in financial services, high tech, military or government institutions and telecommunications sectors, as well as companies that “have been heavily targeted in the past,” according to SANS Institute researchers.
The survey found that many organizations did not have security programs that were mature enough to support threat hunting capabilities. Less than half of respondents, 45%, said their process is largely ad hoc and dependent on what they need; 27% indicated they have defined their own hunting methodology; and 16% do not do any threat hunting. According to SANS, many organizations need more mature threat intelligence capabilities in their security operations centers (SOCs) before they can benefit from hunting practices.
Trained threat hunters presented another hurdle. Only 31% of respondents said their organizations had a designated threat hunting program with assigned staff. About 29% were informal programs, managed by pulling in IT and security operations staff on an ad hoc basis. As the company grows or faces an increasing number of threats, these threat hunting teams are likely to become more permanent, according to SANS researchers. A small percentage of companies, 6%, outsourced their threat hunting to consultants or threat hunting services.
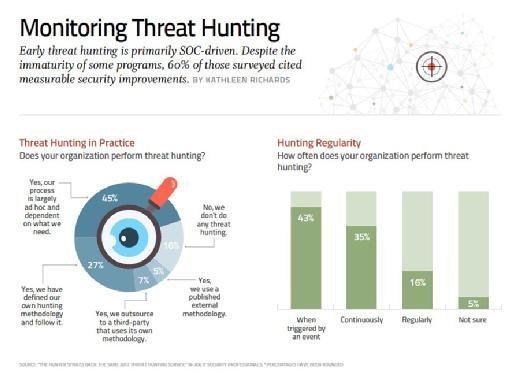
Continuous hunting of threats was also lacking at many organizations. While 35% indicated that their tools and analysts were continuously monitoring for threats, 43% said threat hunting was triggered by an event, alert/alarm or “hunch that something isn’t right.”
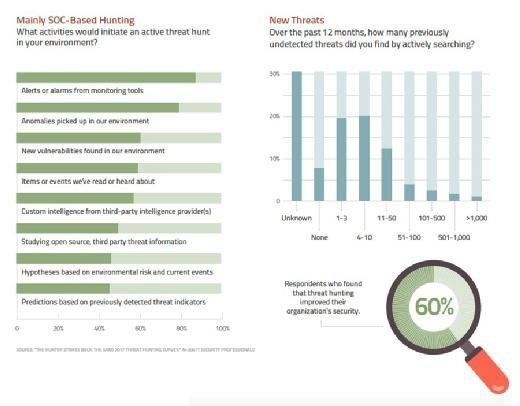
SANS researchers also found that early threat hunting is primarily SOC-driven with less emphasis on cyberthreat intelligence and predictive analytics. Despite the immaturity of some hunting programs, 60% of those surveyed cited measurable security improvements.
